Cyber Risks in Additive Manufacturing Threaten to Unravel the Digital Thread
By Simon Goldenberg and Mark Cotteleer
Wherever data and information are transmitted, used, or accessed, companies must anticipate that someone, somewhere may try to exploit those data and information for personal gain, or to inflict harm or damage. For organizations deploying additive manufacturing (AM) technology, acknowledging this sad reality is not just a business imperative, but potentially a true matter of life and death.
AM is one area where cyber risk poses an especially significant danger. Potential uses for AM span numerous industries as a way to address supply chain challenges associated with unpredictable inventory and expensive-to-produce parts in remote locations. However, the very nature of additive manufacturing technology-with its reliance on digital data files and connectivity to transmit them-leaves it open to significant security exposures, from product malfunctions to intellectual property theft and brand risk, along with other new threats conventional manufacturers may not face.
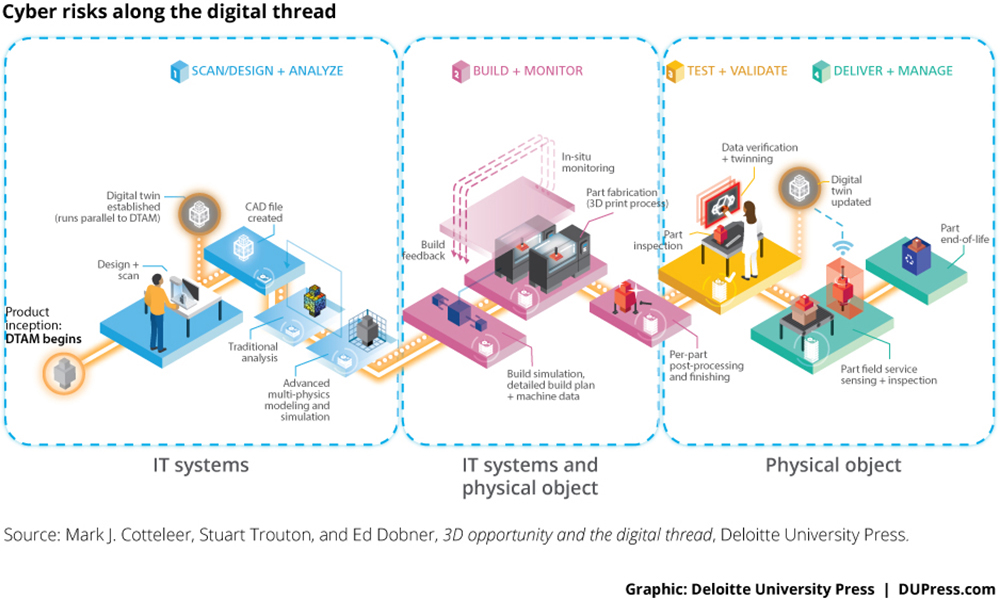
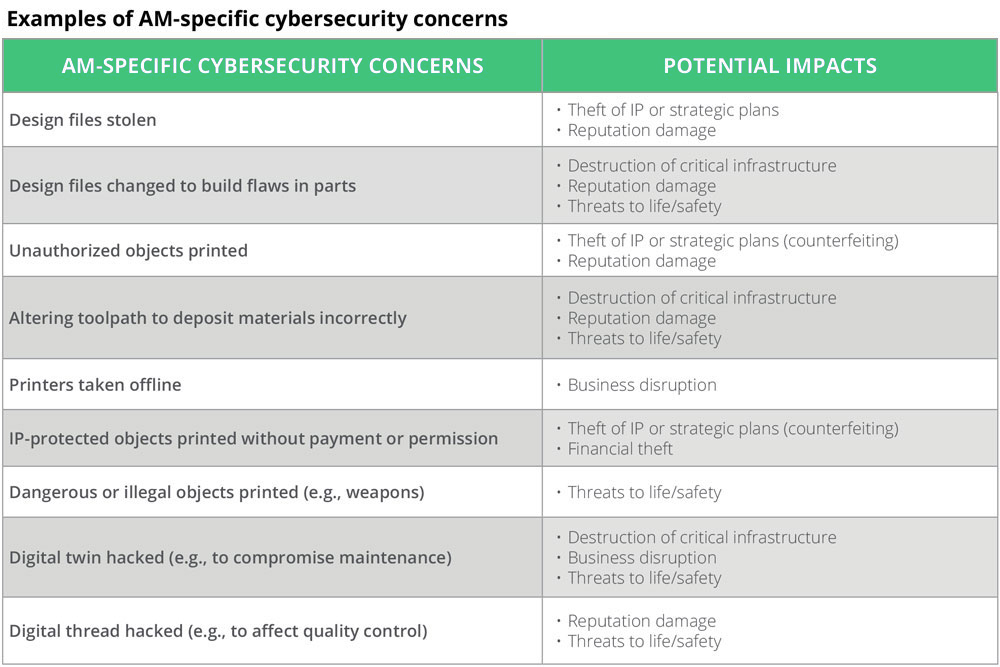 The data generated about an object during the AM design and production processes, for example, can be considerable, generating a strand of information that runs through the AM object’s lifespan known as the “digital thread”. This digital threat holds a trove of technical and operational details of that product. So, if a digital design file is stolen or manipulated, the bad actors can do more than just reverse engineer and illegally manufacture and sell that part. With access to the full design file, hackers could conceivably build in failure points in critical components without the designers’ knowledge.
The data generated about an object during the AM design and production processes, for example, can be considerable, generating a strand of information that runs through the AM object’s lifespan known as the “digital thread”. This digital threat holds a trove of technical and operational details of that product. So, if a digital design file is stolen or manipulated, the bad actors can do more than just reverse engineer and illegally manufacture and sell that part. With access to the full design file, hackers could conceivably build in failure points in critical components without the designers’ knowledge.
“To maintain the integrity of the AM supply chain, organizations must recognize that the intrinsic value of their business may be shifting from the end product to the information that enables that end product.”
The already complicated task of implementing a comprehensive AM cybersecurity protocol is further challenged by the broad reach of the AM supply chain, which extends from suppliers to owners, managers and purchasers of AM systems to distributors and purchasers of AM products. Cyber risk can impact each stage of the digital thread, from design and scan, to quality assurance and printing, to use in the field, and even disposal of the AM objects or printers.
 Value Shift
Value Shift
To maintain the integrity of the AM supply chain, organizations must recognize that the intrinsic value of their business may be shifting from the end product to the information that enables that end product. Securing that value means they must think beyond the file itself and consider all the potential points of entry into the system, and throughout the digital thread, where information may be accessed by unauthorized parties. When one considers that the digital thread extends from design, build, and quality assurance monitoring to testing, delivery, and distribution, the enormity of the cybersecurity challenge in AM is unmistakable.
Manufacturers can look to emerging standards to protect their AM processes during the build process. Leading practices are emerging in the area of tracking and tracing, including the use of RFID tags to track AM-produced products throughout the supply chain. Another promising development is the use of chemicals to apply unique identifiers to AM products; in one case, chemical tags were added to a composite during the build process. While the costs and business processes associated with using these emerging solutions need to be examined, they may show promise in terms of securing products throughout the supply chain and reducing the likelihood of tampering, theft, and counterfeiting. Further, a robust quality assurance methodology can help organizations detect toolpath alterations or other misplacement of materials, among other structural adulterations.
Beyond adding traceable materials during the build process or monitoring quality assurance, organizations can consider putting measures in place to protect the machines themselves. AM printers often do not limit or control who uses them, or what objects are printed. Organizations using AM printers should adopt change management/control workflows for printers and objects, including reviews, and authorized approvals. This allows organizations to have some level of confidence that any objects printed comply with IP rights, license agreements, and other security concerns, as well as that viruses will not be introduced to impact the printer’s function, as with Stuxnet’s impact on centrifuges. AM organizations can model their approach to these workflows on those already in use for other technologies, such as change control boards or configuration control boards commonly used in software management. To ensure an AM printer prints only approved objects, the printer may be isolated on the network, with controls in place to make sure only approved designers can submit files directly to the printer.
Overall, AM offers great promise in terms of democratizing and distributing manufacturing, reducing waste, and enabling rapid production of new and specialty products. There is much work to be done in terms of identifying comprehensive and sustainable AM cyber practices and promulgating them through standards and, where appropriate, additional regulation. Immediate steps such as conducting security risk assessment, developing mitigation plans, encrypting design files, protecting printers and educating stakeholders can go a long way toward understanding and addressing AM cybersecurity concerns now.
Excerpted with permission from:
Deloitte Insights: 3D opportunity and cyber risk management
- Cotteleer, Trouton, and Dobner, 3D opportunity and the digital thread.
- Sturm et al., “Cyber-physical vulnerabilities in additive manufacturing systems.”
- Preeta M. Banerjee and Paul Sallomi, 3D opportunity for technology, media, and telecommunications: Additive manufacturing explores new terrain, Deloitte University Press, December 7, 2015.
- Sturm et al., “Cyber-physical vulnerabilities in additive manufacturing systems.”
Related Resources:
- Deloitte Video Series: Following the digital thread
- Infographic: Trends in additive manufacturing patents
- Article: Additive manufacturing considerations for national security
- Article: 3d opportunity for standards: Additive manufacturing measures up
- MOOC: Additive manufacturing for business leaders
- IDC Forecast: Worldwide Spending on 3d Printing to be Nearly $12 Billion in 2018
